ACTIONABLE THREAT INTELLIGENCE
Digital Shadows provides threat intelligence that delivers for every security team. Its platform was built with today’s overloaded security analyst at heart, who demanded a more relevant and actionable approach to threat intelligence.
Cyber threat intelligence (CTI) improves the resilience of your business against emerging cyber threats. The best CTI program informs preventative and proactive security actions and is intimately tied to business concerns and effective reduction of risk.
SEARCHLIGHT
SMARTER INSIGHT FOR FASTER RESPONSE
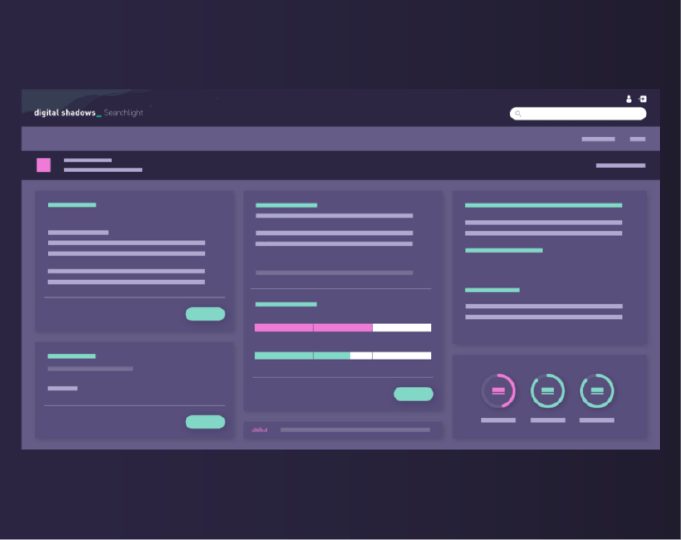
Your security team is busy. Digital Shadows SearchLight removes the noise of Threat Intelligence, making it easier to identify what is important so you can make better decisions faster.
SearchLight provides actionable threat intelligence that adapts to your organization’s specific risk profile and appetite. By combining advanced data analytics, API integrations, and automation features, SearchLight allows your team to take the right action faster.
DON’T LET NOISY DATA BURY THE REAL RISKS
Finding the risks within this vast amount of data is a considerable challenge. SearchLight helps you filter out the noise, automate your response, and focus analyst time on addressing the digital threats most critical to your organization.
HOW IT WORKS
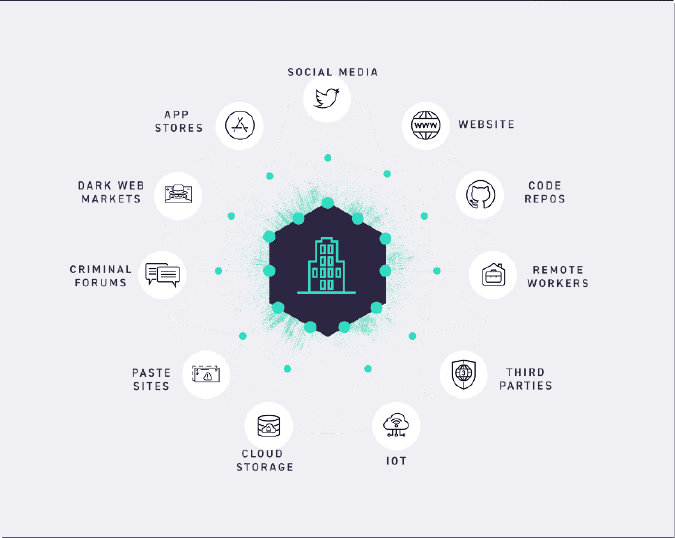
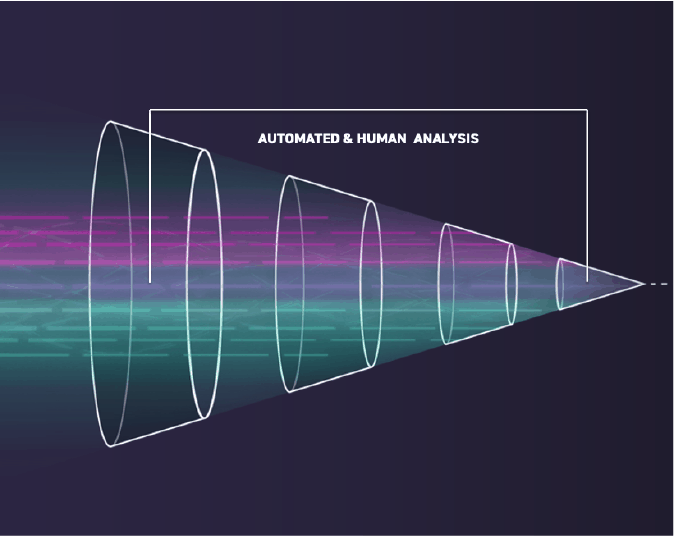
SearchLight has four main stages. At each of these stages, Digital Shadows acts as an extension of your team to help configure your key assets, collect from hard-to-reach sources, analyze and identify risks, and mitigate the impact.
WHAT SETS SEARCHLIGHT APART
Expertise Meets Data
ACCESS
Digital Shadows provides access to the widest range of data sources and the expertise needed to turn that data into intelligence.
Identify What’s Important
ACCURACY
The SearchLight threat model adapts to align our intelligence with each organization’s specific profile and risk appetite.
Intelligent Response
ACTION
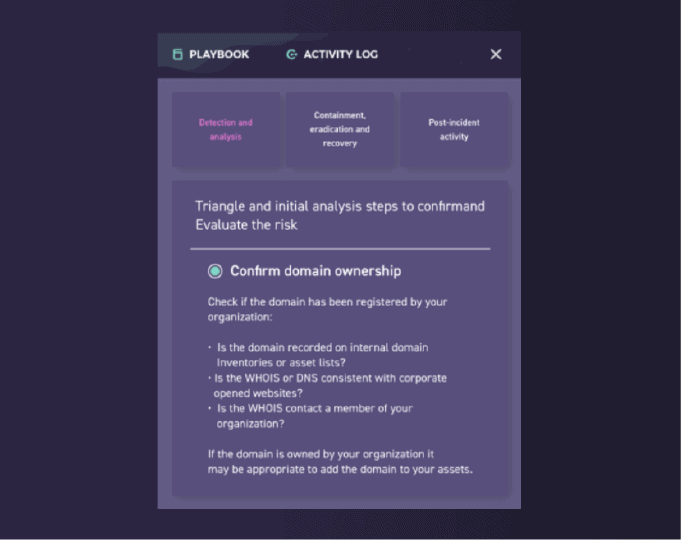
Reduce time-to-triage with SearchLight’s combination of pre-built playbooks and automation features.
SOLUTIONS
Attackers exploit your online brand for phishing schemes, impersonating your brand and executives online to defraud customers, harvest credentials, or spread disinformation. Digital Shadows SearchLight™ proactively identifies instances of brand or executive impersonation, allowing you to react faster. Launch takedowns and prevent damages to customer trust or loss of account credentials.
SearchLight continuously monitors online for brand, company, and executive impersonations, ensuring your brand is secured across the broadest range of open, deep, and dark web sources including technical and closed sources. Neutralize threats to your customers and employees such as business email compromise, phishing sites, and disinformation campaigns with rich context to your exposure. Launch and track takedowns in as little as fifteen seconds with our easy-to-use solution.
Impersonating domains pose a high risk to your organization by leveraging your company name to harvest credentials or defraud customers. Slight variations to your domain names aid attackers in avoiding detection. Digital Shadows SearchLight™ proactively detects all relevant instances of domain impersonation, including typosquat and combosquat domains, and allows teams to launch takedowns faster.
SearchLight reduces the time and manual process necessary to takedown impersonating domains through quick, accurate detection and automated actions. Leverage proprietary technology to get high-confidence coverage and strengthen your defenses.
Attackers leverage social media for phishing schemes, impersonating your brand and executives online to defraud customers or spread disinformation. Digital Shadows SearchLight™ proactively identifies brand and executive impersonations, through immediate detection and takedown services your teams can circumvent damage to customer trust or loss of account credentials.
SearchLight continuously monitors social media sites for security teams to protect their company, brand, and executives. By identifying malicious brand, company, and executive impersonations of your organization as well as threat actor mentions and data leaks, SearchLight ensures threats to your company name and brand(s) online are proactively mitigated.
Whether from an attack or human error from an employee, third party, or contractor, data exposure is inevitable. Digital Shadows SearchLight™ prevents your company from a data breach online by continuously monitoring the broadest range of open, deep, dark, web including technical and close sources. Get high-confidence coverage with accurate alerting to your exposure.
SearchLight proactively identifies credentials and sensitive data exposure online and automates manual processes such as credential validation and takedowns. Quicken response and mitigations to threats to your customers and employees such as account takeover, credential compromise, or exposed sensitive documents with our easy-to-use solution.
With the speed of software development and new product launches, your organization can be just one hasty misconfiguration or unauthorized commit away from exposure. Digital Shadows SearchLight™ protects your organization’s technical data online through continuous monitoring across the broadest range of open, deep, dark, web, including technical and closed sources.
SearchLight alerts your organization in near real time when your access keys, credentials, or source code is exposed online. Through real-time identification and rigorous risk analysis, SearchLight reduces time to remediation by providing security teams with the necessary context and automated actions.
Whether from corporate espionage or inadvertent exposure from an employee, third party, or contractor, intellectual property loss is commonplace. Digital Shadows SearchLight™ protects your organization’s proprietary documents and source code outside of your network through continuous monitoring across the broadest range of open, deep, dark, web, including technical and closed sources. Get high-confidence coverage with rich context to your exposure.
SearchLight detects exposure of and rapidly reduces time to takedown of your organization’s documents, files, or source code. Get automatic risk analysis and unparalleled context such as content analysis in each alert. With real-time notification and rich context around your intellectual property exposure, security teams can quickly identify sources and automate takedowns all within one platform.
Your organization interacts with hundreds, if not thousands, of third party vendors and suppliers, meaning infinite possibilities of data compromise and reputational damage. Digital Shadows SearchLight™ gives you unparalleled visibility of your exposure via third parties inclusive of exposed data and credentials. Get immediate reporting and analysis on the latest breaches and take quick action against third party data breaches.
SearchLight continuously monitors the open, deep, and dark web, including closed and technical sources, for third party data breaches relevant to your organization. Eliminating the time and resources necessary to index online file stores and billions of dark web pages, SearchLight acts as an extension of your team delivering accurate alerting with access to an extensive threat intelligence library to proactively reduce third party risk.
Today’s threat landscape evolves faster than ever, and security teams need to understand how to best respond to emerging techniques relevant to their organization, sector, and geography. Digital Shadows SearchLight™ acts as your organization’s threat intelligence unit, combining the expertise of our world-class threat intelligence research team and closed-forum analysts to answer your intelligence requirements. Get your threat intelligence program to the next level with a single-source for your organization’s tactical, technical, and strategic intelligence.
SearchLight aligns your team with a top-tier Threat Intelligence unit. Proactively prevent breaches by exporting IOCs from active threat actors, malware, and events and identify security gaps via MITRE mappings and associated techniques. Access a continuously updated Cyber Threat Intelligence library, compiling over 10+ years of threat intelligence reporting and dark web data with over 2,000+ threat profiles on the latest threat actors, campaigns, criminal locations, and techniques.
The dark web is often the first place your organization’s breached data lands— from compromised credentials, third party leaks, ransomware dump listings. It also is a source for invaluable threat intelligence— pre-planned attacks or discussion around vulnerabilities and exploits. Digital Shadows SearchLight™ gives you unparalleled visibility into dark web risks to your organization, enabling teams to take actions on threats before they become incidents.
SearchLight continuously monitors the broadest range of dark web sources for threats to your organization, including restricted cybercriminal forums in English, Russian and Mandarin through our dedicated team of global analysts. Eliminating the time and resources necessary to index hundreds of millions of dark web pages, SearchLight acts as an extension of your team delivering accurate alerting with access to an extensive threat intelligence library and historical archive of dark web data spanning 10+ years.
Digital Shadows Searchlight proactively identifies vulnerabilities to your organization, allowing your team to prioritize and patch the most critical vulnerabilities with rich context into reports of exploitation. Gain instant context with unlimited searches through raw, indexed threat data and finished Digital Shadows intelligence.
SearchLight continually identifies exploitable vulnerabilities on your public infrastructure through custom prioritization that goes beyond CVSS scoring. In addition to immediate alerting of newly discovered vulnerabilities, teams can search our historical data archives of 10+ years and curated library of finished intelligence for thousands of threat actors. With SearchLight, your organization can effectively prioritize the vulnerabilities that pose the greatest threat to your organization.