Delivering modern cybersecurity by proactively safeguarding critical data and IP
Forcepoint is the leading user and data protection cybersecurity company, entrusted to safeguard organizations while driving digital transformation and growth. Forcepoint’s solutions adapt in real-time to how people interact with data, providing secure access while enabling employees to create value.
Forcepoint ONE is the all-in-one cloud platform designed to protect a hybrid workforce and the information they access on the web, via the cloud and in private applications.
Forcepoint ONE unifies three foundational gateways: Secure Web Gateway (SWG), Cloud Access Security Broker (CASB) and Zero Trust Network Access (ZTNA). Together, these three services make up what Gartner terms the Security Service Edge.

Are you juggling multiple cybersecurity tools?
Fighting threats is hard enough without the battle you fight every day. The battle to keep your head above water while managing multiple security solutions.
Maybe you don’t need to adopt more tools – just the right one.
Let’s fight the complexity of security together.
Enter Forcepoint ONE — the platform born in the cloud, for the cloud. It’s an all-in-one console that contains today’s security essentials but can scale to meet tomorrow’s needs.

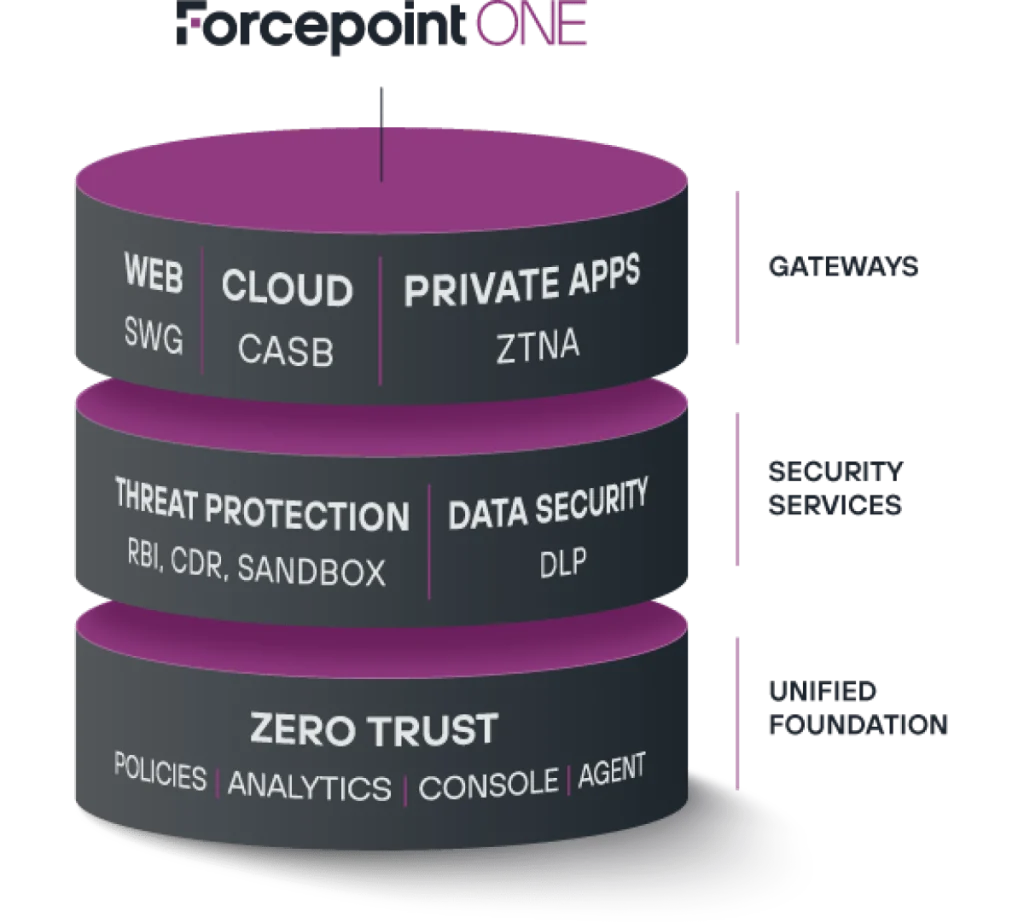
Here’s a bit more about Forcepoint ONE’s three foundational gateways:
- Secure Web Gateway – This is the service that monitors and controls any interaction with any website. This includes blocking access to websites based on category and risk score, blocking download of malware, blocking upload of confidential or sensitive data to personal file sharing accounts and detecting shadow IT.The Forcepoint ONE SWG features a unified agent that runs locally on Windows and macOS devices to enable smart routing of web traffic, offering up to 2x the throughput of our SWG competitors.
- Cloud Access Security Broker – Back in 2013, Bitglass started as a CASB company that differentiated itself from the competition through its true reverse proxy mode. And that advantage continues. Forcepoint ONE uses this leading agentless CASB solution to control access to managed cloud applications and to shadow IT applications. It also provides data loss protection (DLP) and malware protection as well.The Forcepoint ONE CASB can be configured to integrate with any SIEM tool that supports syslog, or to integrate with any on-premises DLP systems that supports ICAP. It also supports two-way integration between Forcepoint ONE and selected Security Orchestration Automation and Response (SOAR) platforms. Finally, Forcepoint ONE CASB can use classification metadata from any data classifier in a DLP match pattern.
- Zero Trust Network Access – This gateway controls access to private applications hosted behind a firewall—something it does without the need for virtual private networks (VPNs). Like CASB does for traditional cloud apps, ZTNA provides DLP and malware protection for private web-based applications.
Work safely at warp speed
A lot is happening on the endpoint. That’s why Forcepoint ONE is there too. It’s the platform that routes traffic locally and puts security measures on-device. Decryption, inspection and blocking are all happening where the work happens – all without impacting users.
Secure work on any device
Nearly everyone’s working on multiple devices. What’s not working? Using multiple solutions to secure all of those devices. Forcepoint ONE is one console with many solutions. From one platform, gain visibility, control access and protect data on all devices.
Protect managed and unmanaged apps
Give access to only the apps a user needs rather than the entire network. Protect managed or unmanaged apps with full-strength encryption in-app. Detect zero-day threats at upload, download and even when data is at rest. Block data leaks in files, images or text and stop malware from a device or browser.
An all-in-one, total solution
Secure Web Gateway
This cloud SWG is on-device and directs traffic locally. No need for on-prem appliances, VPNs or network hops.
Cloud Access Secure Broker
Everything’s moving to the cloud – including data. Keep it all safe with an industry-leading CASB.
Zero Trust Network Access
Agentless access for browser apps and BYODs are simpler to manage and deploy. Restrict access per user and per app.
Cloud Security Products
Complete security for all cloud applications. Period.
- Complete visibility into shadow IT: Identify and categorize cloud apps to access risk and pinpoint which services to allow and monitor with Forcepoint Cloud Access Security Broker (CASB).
- Prevent compromised accounts: Stop bad actors from accessing cloud application data. Use leading machine learning and UEBA capabilities to establish behavioral fingerprints for advanced risk calculation.
- Secure mobile access to cloud apps: Apply unique access and security policies on a per-device basis by easily distinguishing between managed and unmanaged (BYOD) devices.
Making the web safe for every user, anywhere.
- Stop advanced threats hidden in dynamic web content: Proactively secure the web with advanced, real-time threat defenses—full content inspection and in-line security scanning help mitigate risk and protect against malware.
- Advanced threat protection powered by ACE: Keep users safe from malicious threats, including zero-day threats. Protect against zero-day threats with real-time threat intelligence and remote browser isolation, and provide deep content inspection for encrypted and unencrypted traffic to detect evolving threats across the entire kill chain.
- Prevent theft of regulated data and intellectual property: Forcepoint’s Web DLP module provides the industry’s leading DLP engine (Forcepoint Enterprise DLP) to protect against data exfiltration over the web in real-time.
- Safe access for every user, anywhere: Ensure security policies are consistently enforced for all users at all times – whether traveling, at home, or on the corporate network.
- Industry’s strongest cloud infrastructure: Private peering partnerships with the most Tier 1 networks for faster connectivity and over 160 PoPs across 145 countries for localized content.
- Move to the cloud at your own pace: Choose when, where and how you deploy. Choose where and how you connect to the cloud.
Continuous Zero Trust Security
Automatically control access and usage based on your people’s own behavior
Replace implicit trust with explicit permission verified every time
With your people working remotely, keeping your enterprise systems and data secure requires a new approach. Zero Trust helps you more effectively:
- Stop threats from moving within your network
- Control usage of data—not just access
- Continuously know who’s creating risk
Data-First SASE
The industry’s only solution uniformly protecting data from the endpoint to the cloud.
Secure Access Service Edge (SASE) is a new approach to networking and security that reinvents these technologies as converged cloud services. It provides uniform connectivity and protection everywhere so that people can work anywhere.
Forcepoint’s SASE goes beyond just securing access to web, cloud, and private applications. We put our industry-leading data protection at the center of our SASE platform, giving you unique control over how your data is used even after it is downloaded. We help you make your people more productive and your business safer.
Protect workers anywhere against advanced threats with cloud-delivered SASE
- Keep malware out of downloads
- Eliminate security gaps across web, cloud, networks, private apps
- Control access based on the risk a resource presents
Prevent loss of data everywhere it’s used, endpoint-to-cloud
- Write policies once and use a SASE architecture to enforce them everywhere
- Stop transfers of data with enterprise-grade DLP technology
- Implement Zero Trust-as-a-service
Reduce complexity and cost with a converged SASE platform
- Simplify deployment with a unified agent for endpoints
- Safely connect remote sites to the cloud with secure SD-WAN
- Automate and personalize enforcement based on risk
Data Security Products
Secure your data while enabling productivity
Data protection does not have to get in the way of business productivity. Forcepoint’s focus on unified policies, user risk, and automation makes data security frictionless and intuitive.
- Control all your data with one single policy: Replace broad, sweeping rules with individualized, adaptive data security that doesn’t slow down your employees. Block actions only where you need to, and drive productivity
- Simplify compliance with predefined policies: View and control all of your data with the industry’s largest pre-defined policy library. Ensure regulatory compliance across 80+ countries for GDPR, CCPA and more. Deploy data classification with Boldon James and Azure Information Protection.
- Protect critical intellectual property with unsurpassed accuracy: Protect PII and PHI, company financials, trade secrets, credit card data, and other pieces of sensitive customer data-even in images. Follow intellectual property (IP) in both structured and unstructured forms, and stop low & slow data theft even when user devices are off-network.
- Prevent data breaches automatically: Automatically block actions based on an individual user’s risk level with risk-adaptive data protection.
Threat Protection Products
Isolate malware from the endpoint and protect users on the web
Elevate your security posture by taking a Zero Trust approach to web security with Forcepoint RBI and allow safe interaction with unsafe sites.
- Upgrade to Zero Trust web security with Remote Browser Isolation: Web Security tools are good at blocking access to unsafe sites, but sometimes organizations just have to work with unsafe sites regardless of the risk. A Zero Trust approach to web security is the answer. When you need high assurance protection to allow safe use of unsafe sites there is no better solution than Zero Trust web security using Forcepoint RBI.
- Automatically balance security with performance to drive user adoption and ease management: Smart Isolation automatically switches between Secure Streaming and Secure Rendering RBI modes to balance security and performance based on the contents of the webpage. Embedded intelligence removes the worry of when to use each mode while also optimizing end-user experience.
- Automatically sanitize files as they are downloaded using Zero Trust Content Disarm and Reconstruction (CDR):
Gain assurance that files can be safely downloaded from any website and used, even if they contain malware. Zero Trust CDR reconstructs files in the original format using a process that neutralizes and filters out any potentially unsafe elements. - Prove heightened security with the Threat dashboard: Uniquely detailed insights on the threats prevented via RBI provides better ROI insights and help inform security teams of the active threats being faced by the user population.
It’s time to pivot from detection to prevention.
Rather than trying to detect malware, Zero Trust CDR works by extracting the valid data, verifying the information and then building brand-new data.
- Ensure all data is safe: Rather than trying to detect malware, Zero Trust CDR uses a unique process of transformation to only deliver the valid business information users need.
- Protect against multiple attack vectors: Deploy on the boundary to ensure Web browsing, email, file upload, file sharing and Web applications are always malware-free.
- Enhance user experience: Deliver pixel perfect, fully revisable, malware-free files in real time, with no delays for scanning or sandboxing.
- Reduce pressure on the Security team: There are no false positives for the security team to deal with and the unique way that CDR works means there’s no need to keep patching with signature updates to combat the latest malware.
Superior protection against zero-day threats with advanced sandboxing
Detect and stop today’s evasive malware
Go a step beyond sandboxing with Deep Content Inspection—reveal activity and dormant code that often gets overlooked.
Simulate an entire host, including the CPU and system memory, with our unique isolation and inspection environment.
Correlate incident information and prioritize significant threats—without combing through log files.
- Prioritize risk with correlation: Detail exposure allows you to do more than just stop malware—quickly coorelate incident information to prioritize significant threats.
- Protect your network: Detect threats other tools miss and eliminate false positives with the industry’s most accurate AI-powered threat detection.
- Complement your security stack: Integrate with Forcepoint CASB, NGFW, Web Security, and Email Security solutions—share intelligence and strengthen each point of defense.
- Track all malware: Observe all the actions malware takes, even when they are delegated to the operating systems or other programs.
- Get full chain visibility: Quickly understand the scope of a breach to expedite notifications and remediation efforts.
- Deploy how you want: Available as a cloud service, on-prem, or as an air-gapped solution with Forcepoint NGFW for physically isolated network requirements.
Network Security Products
Don’t Let Your Firewall Box You In
Get security, availability and visibility with Next-Gen Firewall
Top-Rated NGFW and secure SD-WAN
Blocking 100% of evasion attempts and 99.1% of exploits, Forcepoint NGFW was given a AAA rating when tested by CyberRatings.
Do More with Less with Forcepoint Next-Gen Firewall
- Greater security with less disruption: Built-in Secure SD-WAN, zero trust network access controls and the ability to push out unified policies globally with one click empowers your team to manage and maintain a secure network at scale.
- Get ahead of breaches by lowering your exposure: With one central console, you gain 360-degree visibility which lets you quickly identify risks. And industry-leading integrated intrusion detection and prevention helps you mitigate them before they become a problem.
- Reduce Total Cost of Ownership (TCO): Cut down on redundant tasks. With advanced automation, you can get updates and upgrades on your schedule. Plus with a single management console, you can make changes on a global scale.
- Deploy from anywhere: Advanced tooling allows you to automate, orchestrate and accelerate your network architecture – remotely and at scale.
- Hybrid-ready, multi-cloud enabled: Designed like software, rather than hardware, NGFW gives you the flexibility to deploy on hardware, virtually or in the cloud. Open API’s let you customize automation and orchestrations to your own specifications.
- Continuously battle-tested: Our products routinely undergo rigorous certifications testing to meet the most stringent needs of sensitive and critical industries, agencies, organizations and governments around the world.
Secure and Reliable SD-WAN
Manage and securely connect all remote offices and branches from a central console.
A seamless network and a secure consistent connection
Confidently connect and protect remote sites at a global scale. You can do it with Secure SD-WAN conveniently built in to our Next-Gen Firewall
Resilient and smart
Keep the entire workforce connected. Secure SD-WAN is built with multiple redundancies and a system that intelligently load balances and manages traffic.
Zero touch upgrades
Simplify setup and management of SD-WAN at scale. Updates and upgrades can be scheduled and without a need for staff to be on site.
Reduce risk
Connect and protect branch offices and remote sites on a global scale quickly from a centralized management console.

