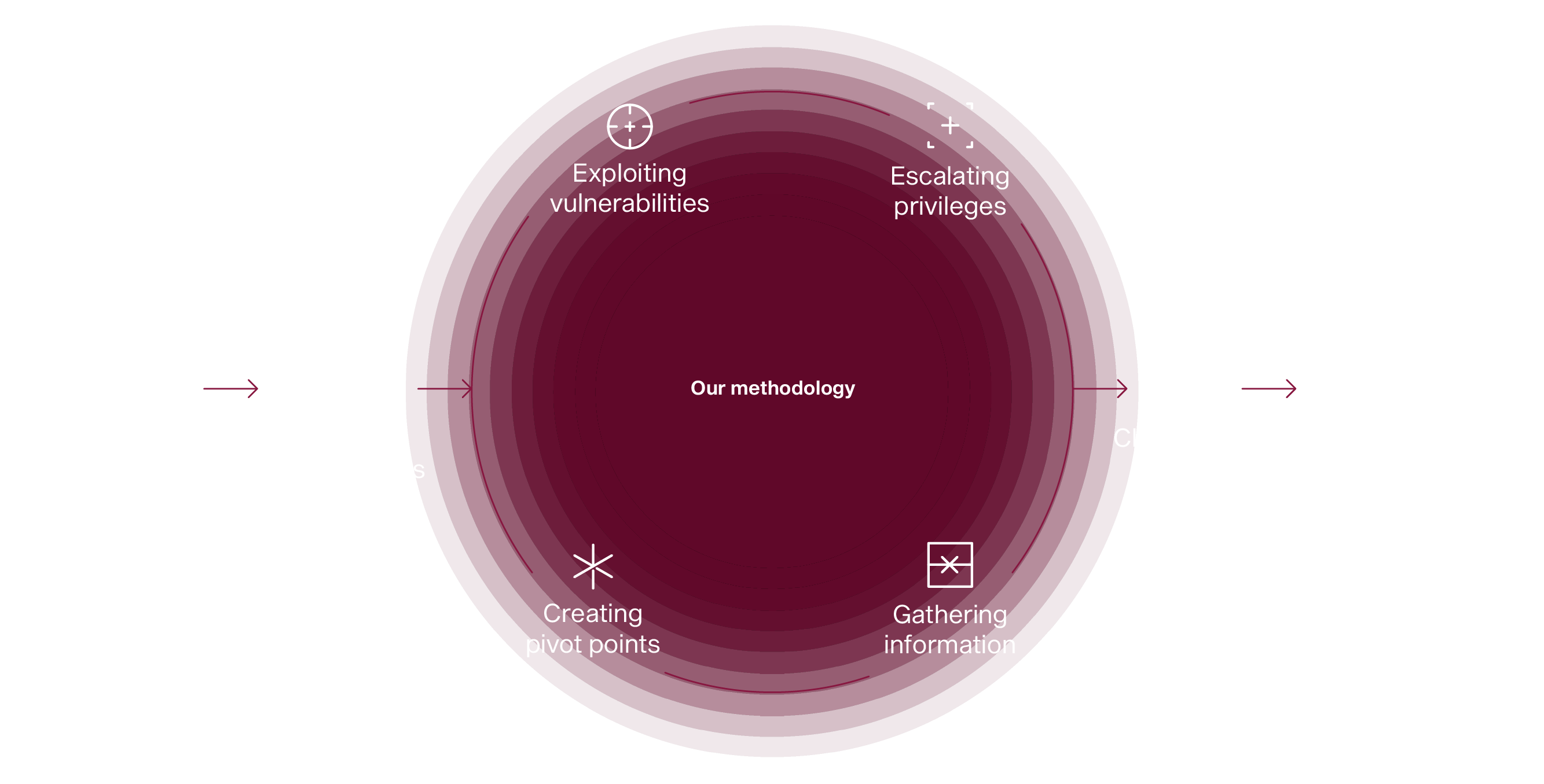
A deeper overview.
Being not a conventional security firm, Faraday focuses on cutting edge offensive cyber security techniques that go far beyond standard scanning to uncover vulnerabilities that others miss.
Faraday works with companies that look for that extra mile, those who understand the importance of security and are looking for a deeper overview of their security posture to ensure that no rock is left unturned.
Pioneers in Vulnerability Management
Founded in 2004 by researchers Faraday leveraged all their research and consulting expertise into a platform that promotes collaboration among security experts.
Community-driven and proud of it
Founding members of Ekoparty security conferences, the largest cybersecurity conference in Latin America. Faraday’s specialists are speakers at the most respected security research conferences such as Defcon, BlackHat, Shakacon and H2HC among others.
In-house Research Lab
A team of experts solely dedicated to researching cryptography, forensics, electronics development and reverse engineering.
Faraday Rethink Vulnerability Management
Faraday provides a smarter way for Large Enterprises, MSSPs, and Application Security Teams to get more from their existing security ecosystem.

Normalize and Integrate security tools
Get vulnerability data from more than 80 scanning tools.
Faster vulnerability managing and prioritization
Built around collaboration, manage, tag, prioritize with ease.
Automate with Agents and Workflows
Automate vulnerability response to remediate faster.
Reduce and prioritize
An interface built around collaboration and simplicity: manage, tag, prioritize with ease.
Faraday CLI
Allows users to access Faraday information directly from the terminal.
Actionable Reporting and Vulnerability Templates
Every company has a different approach to reporting. Faraday provides a way for companies to export their data into their own compliance-ready formats.
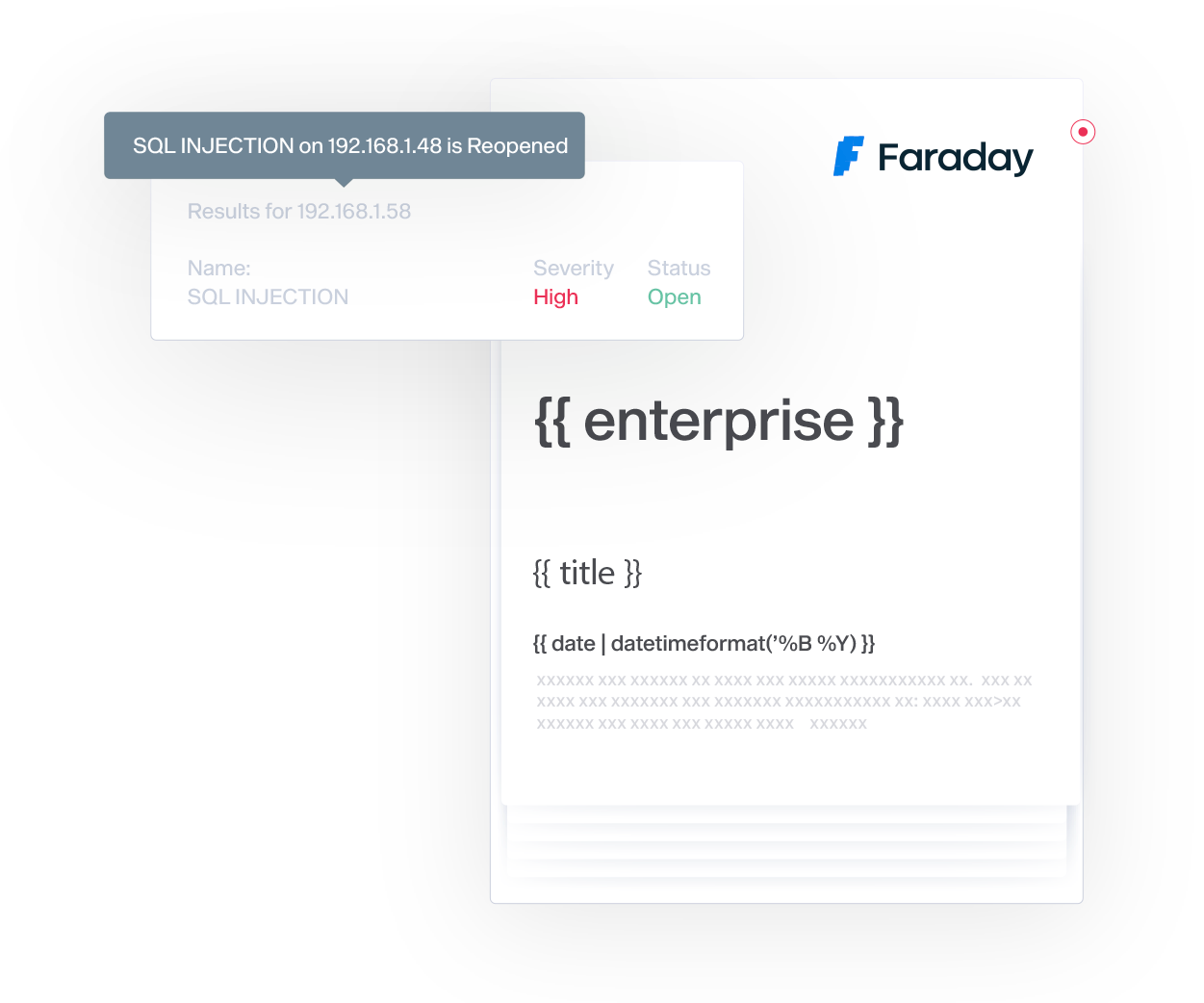
Custom Workflows and Seamless Deduplication
Trigger any action with custom events built to avoid repetitive tasks. Import all your data and never worry about duplicates, as Faraday automatically identifies and merges duplicated issues.
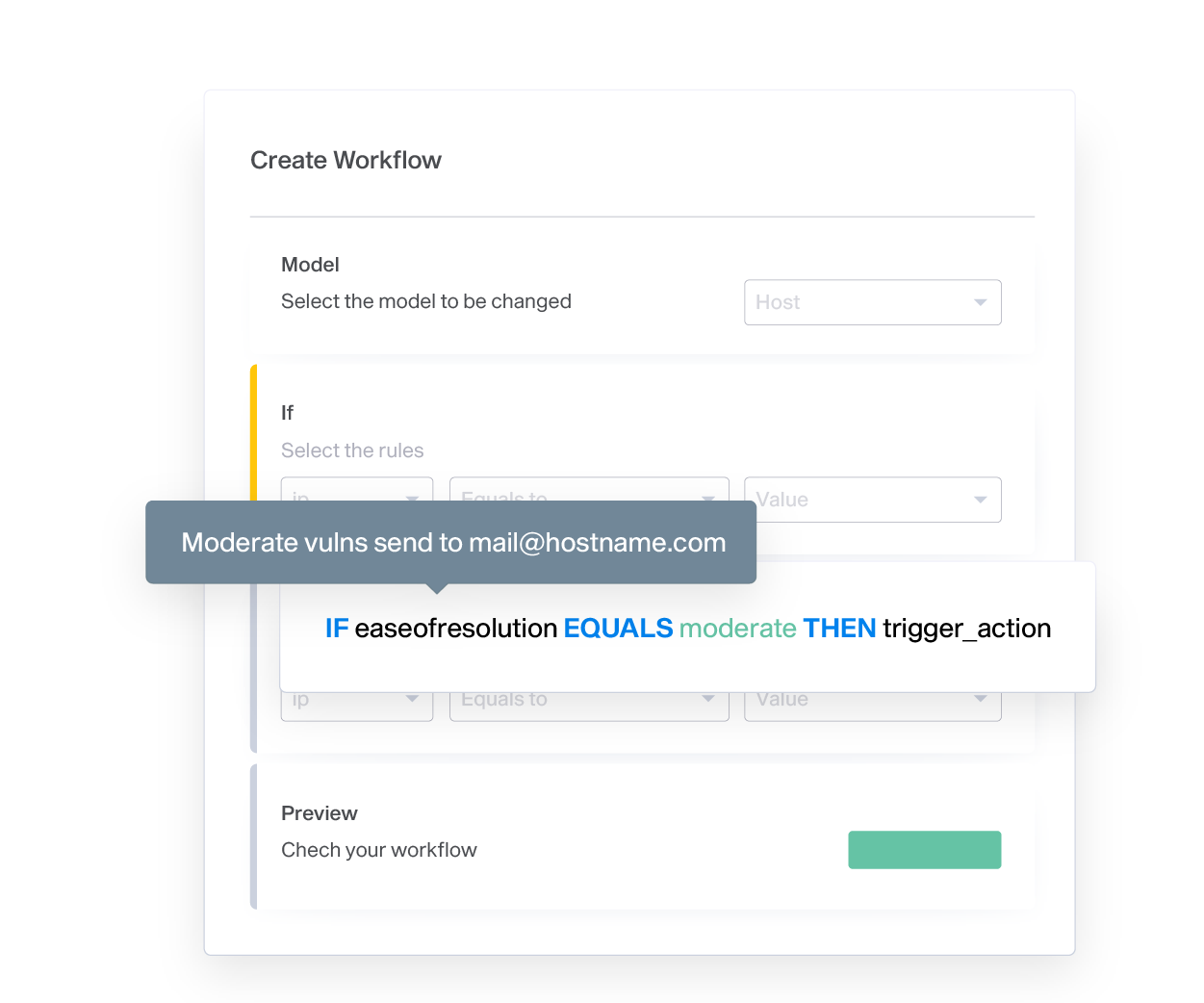

Easily Schedule Scanners and Jobs with Agents
Agents are a lightweight, highly-scalable way to automate repetitive scheduled scans or triggered jobs that unnecessarily take up team resources.
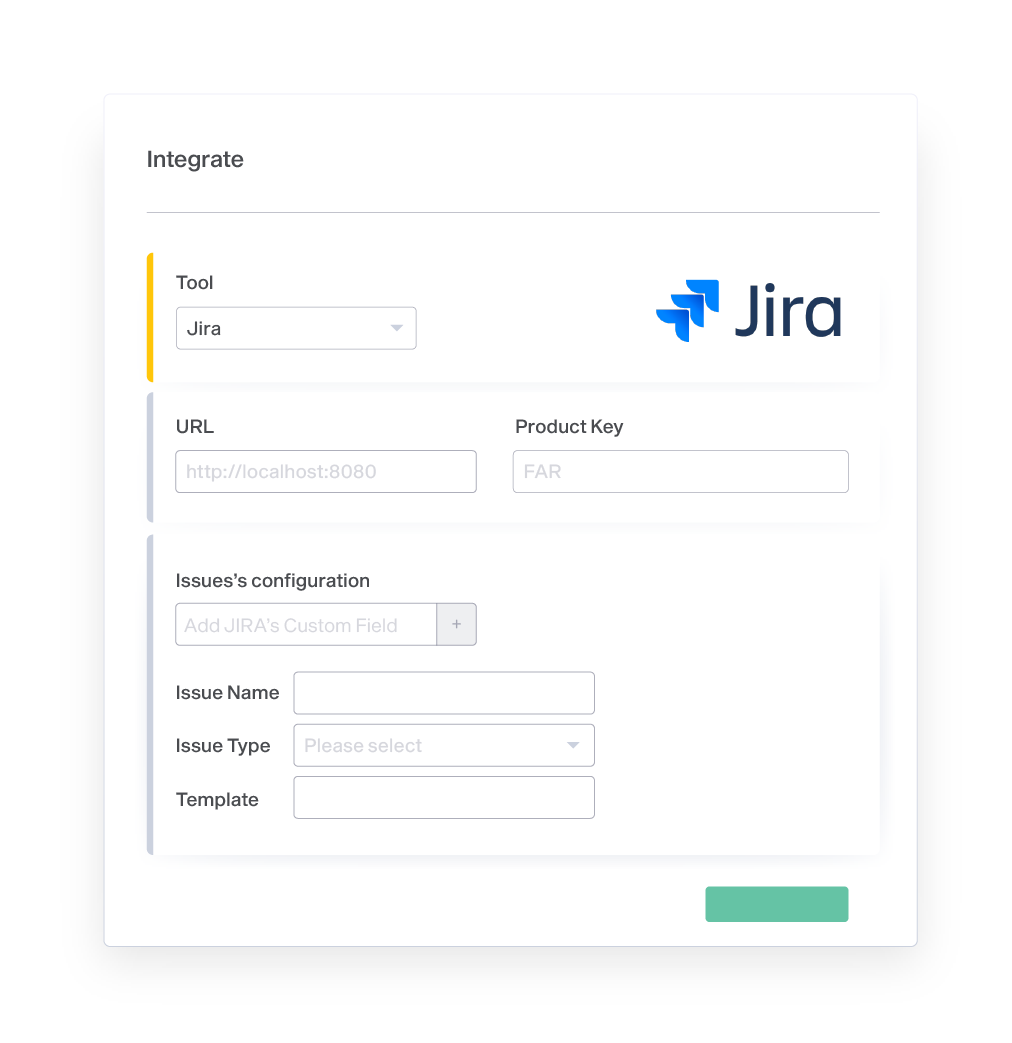
Jira, ServiceNow, 2nd Factor Authentication (2FA) and LDAP
Synchronize your favorite ticketing systems (JIRA, ServiceNow) and integrate with your existing Direct Access Protocol (LDAP).
Faraday is continuously adding new integrations based on customer requests.
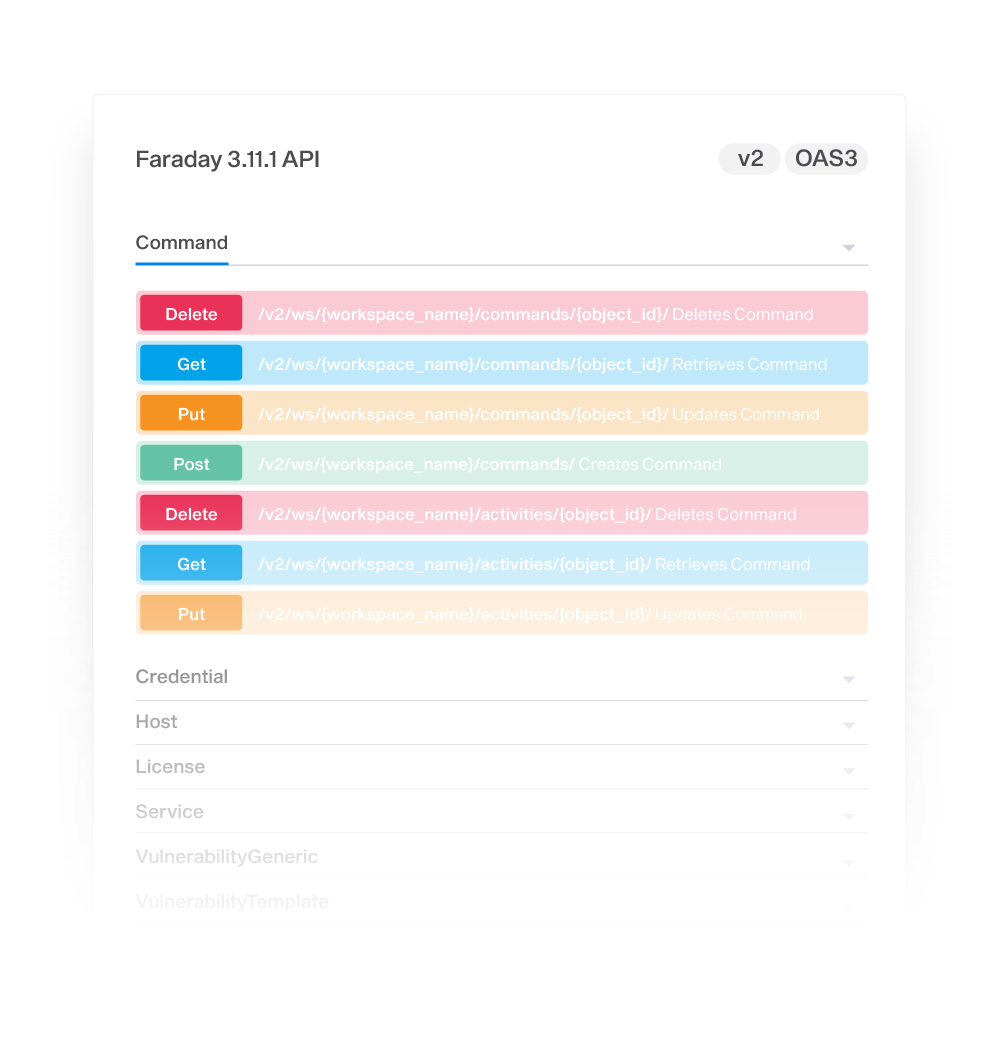
Easy-to-use REST API
Leverage Faraday’s REST API to scale your own strategy by directly accessing integrations, analytics capabilities, and reporting depending on your needs.
Services
Faraday has deep cross-platform expertise
Your apps are the most common gateways for security weaknesses. We use a comprehensive suite of technical solutions to perform a professional assessment that guarantees a real map of vulnerable vectors.
Authentic Red Team in action. The art of deconstructing to rebuild the original equation. A reverse ride allows you to extract sources of real cyber threats for your most valuable applications.
Your Applications can suffer a cyber-attack just like your Networks. We analyze your mobile architecture giving you a comprehensive map of vulnerable areas to remediate.
The health of your networks compromises the health of your company. Our technical Red Team performs an exhaustive analysis detecting areas of critical risk.
Hardware and Software Security is not complete without closeness. An offensive art focused on detecting potential failures reviewing your on-site infrastructure.
Using the same techniques an adversary would use, we recreate a real attack environment to conquer the most vulnerable assets and areas of your infrastructure.
Vulnerabilities are identified directly in your code, reviewing the software quality assurance. *We classify* them by risk, with advice on the best way to mitigate the general impact on your organization.
Internal customers are one of the most vulnerable attack vectors in your company. By working with an authorized intrusion attempt, you can verify the right workstation set up and the awareness level to enhance security policies.