Endpoint Protection for the Modern Enterprise
In today’s mobile world, endpoints are the new perimeter—and every endpoint is a possible beachhead for a larger compromise. Carbon Black gives you the endpoint protection you need to disrupt advanced attacks before they compound.
With the continuously evolving threat landscape, settling for a checkbox on security is laying out a welcome mat for cyber-attacks. Whether you’re looking to replace antiquated malware prevention or want to empower a fully-automated security operations process, VMware Carbon Black fully meets your needs.
VMware Carbon Black Cloud Products

VMware Carbon Black CloudTM
Cloud-Native Endpoint Protection Platform (EPP)
VMware Carbon Black’s cloud–native endpoint protection platform combines the intelligent system hardening and behavioral prevention needed to keep emerging threats at bay.
- Replace legacy antivirus with lightweight prevention that adapts to your business.
- Detect and prevent attackers from abusing legitimate tools.
- Automate your investigation workflow to respond efficiently

Endpoint Standard
Next-Generation Antivirus and Behavioral EDR
Cloud-Native endpoint protection that combines prevention and automated detection to defend against today’s advanced cyber attacks from a single agent and console.
- Block malware, ransomware, non-malware, living off the land and other emerging, never-before-seen attacks automatically, both online and offline.
- Simplify deployment and operations with out-of-the-box policies and easily adapt protection to your organization.
- Visualize every stage of the attack with easy-to-follow attack chain details to uncover root causes in minutes.

Enterprise Endpoint Detection and Response
Threat Hunting and Incident Response
Cloud-native threat hunting and incident response (IR) solution delivering continuous visibility for security operation centers (SOC) and IR teams.
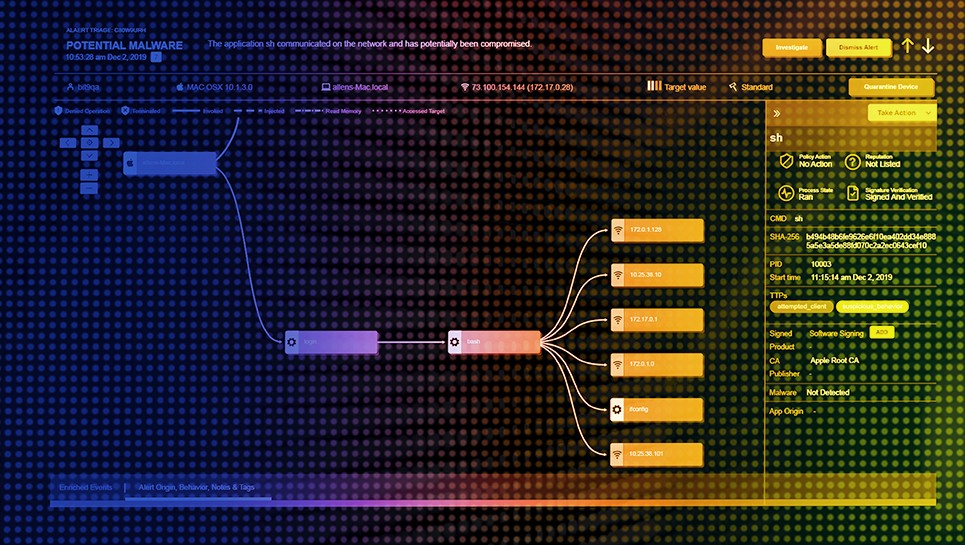
- See what happened at every stage of an attack with intuitive attack chain visualizations and uncover advanced threats and minimize attacker dwell time.
- Leverage cloud-delivered threat intelligence and custom watchlists to automate repetitive hunts.
- Isolate infected systems and remove malicious files to prevent lateral movement.
Audit and Remediation
Real-time Device Assessment and Remediation
Easily audit current system state to track and harden the security posture of all your protected devices.
- Gain visibility into precise details about current state of all devices – on and off the network.
- Close the gap between the security and infrastructure teams, allowing administrators to perform comprehensive investigations and remote remediations.
- Allow administrators to automate ongoing reporting on patch levels, user privileges, disk encryption status, and more to track and maintain a desired posture.

Managed Detection
Managed Alert Monitoring and Triage
Gain round-the-clock eyes on glass from our SOC of expert analysts, who provide validation, context into root cause, and automated monthly executive reporting.
- Gain alert coverage and threat triage across your entire deployment.
- Leverage Global threat intel to stay a step ahead of outbreaks.
- Augment your team with advanced threat hunting and incident response by world-class experts.
VMware Carbon Black On-Premises Products
App Control
Application Control and Critical infrastructure protection
VMware Carbon Black App Control is an industry-leading application control product, used to lock down servers and critical systems, prevent unwanted changes and ensure continuous compliance with regulatory mandates.
- Harden new and legacy systems against malware, ransomware, zero-day and non-malware attacks with broad support for embedded, virtual and physical operating systems.
- Secure end-of-life systems with powerful change control and allowlisting policies.
- Out of the box templates based on industry best practices keep management overhead low.

Endpoint Detection and Response
Detect and Respond to Advanced Attacks at Scale
Threat hunting and incident response (IR) solution delivering continuous visibility into hybrid deployments for top security operations centers (SOC) and IR teams.
- Collect and visualize comprehensive information about every monitored endpoint. Give security professionals greater visibility into their environment.
- Consolidate threat intelligence for your environment to automatically detect suspicious behavior.
- Isolate infected systems and remove malicious files to prevent lateral movement and store detailed forensic data for post-incident investigation.

