‘Continuous Compliance’: The Evolution and Benefits for Modern Cyber Security
Introduction
In today’s rapidly evolving cyber landscape, maintaining compliance with regulatory standards is a complex yet critical task for enterprises and government agencies alike. Continuous Compliance, a cyber security term first coined by Andrew Curtis nearly 20 years ago, has become a cornerstone in the architecture of cyber uplift programs. This concept is not merely about adhering to regulatory standards; it’s about creating a dynamic, real-time approach to compliance that integrates deeply with an organization’s operations and security practices.
Origins of Continuous Compliance
The idea of Continuous Compliance emerged from the need to address the ever-increasing complexity of cyber threats and the regulatory environment. Andrew Curtis, during his early cyber consulting work, recognized the inefficiencies and gaps in traditional compliance approaches. These methods were often static, manual, and reactive, leaving organizations vulnerable to emerging threats and compliance lapses.
Continuous Compliance was developed as a proactive, integrated solution that combines regulatory compliance with operational security. This approach was designed to ensure that compliance is not a periodic checkpoint but a constant state of readiness and adaptability.
What is Continuous Compliance?
Continuous Compliance refers to the integration of compliance activities into the daily operations and security protocols of an organization. This involves using automated tools and processes to ensure that compliance is continuously monitored, managed, and enforced. Here’s an example of a Continuous Compliance architecture. Note the cyclical nature of asset integration, scanning, detection, federation and management.
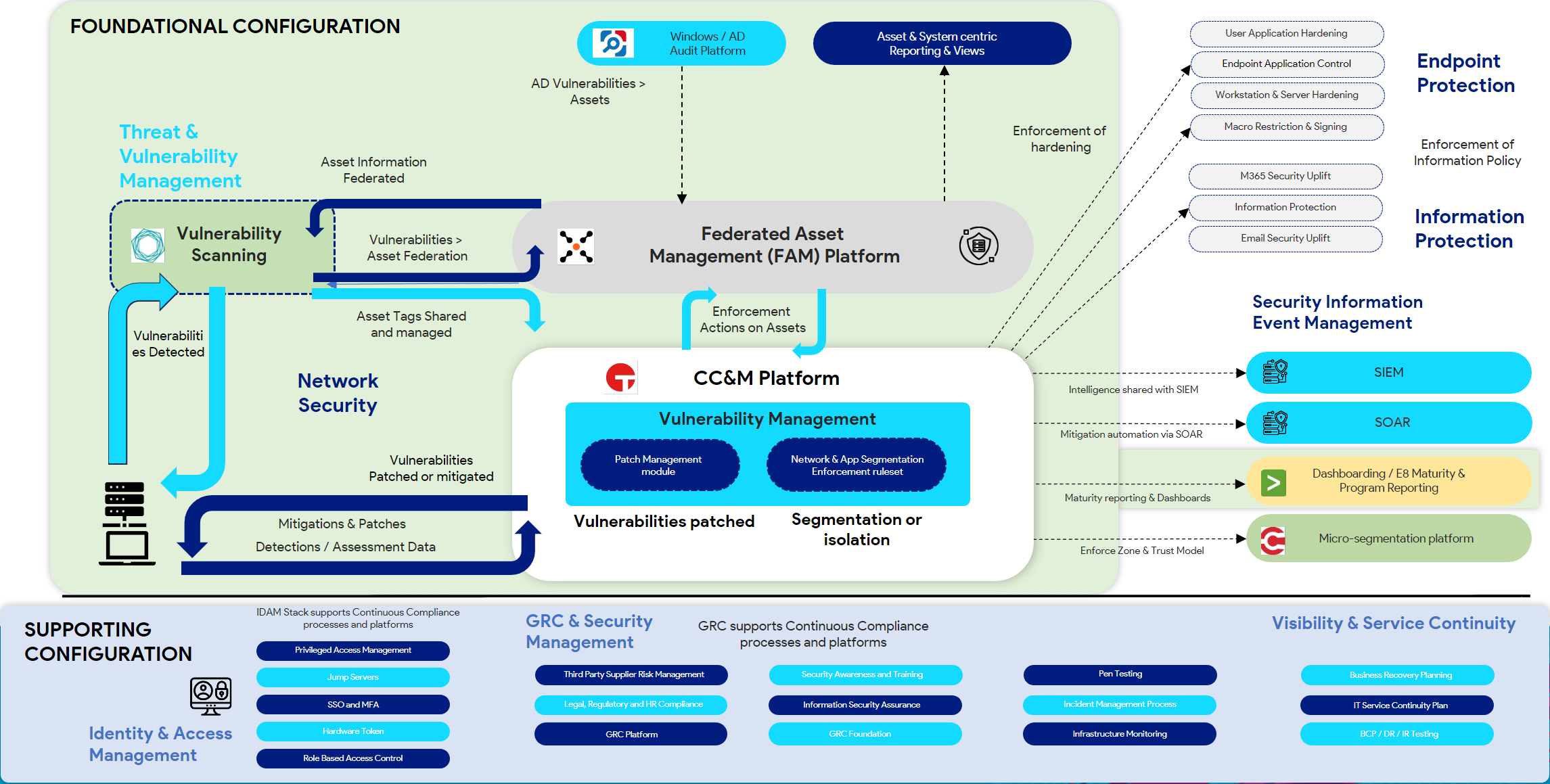
Key features include:
- Real-Time Monitoring and Reporting: Continuous visibility into the compliance status across all assets and systems.
- Automated Compliance Actions: Immediate remediation actions for compliance deviations detected through automated systems.
- Integrated Compliance and Security: Unifying compliance requirements with security operations to ensure a cohesive approach.
- Dynamic Adaptation: Continuously adapting to new threats and regulatory changes without the need for significant manual intervention.
Features of Continuous Compliance
- Enhanced Visibility: Continuous Compliance provides a holistic view of an organization’s compliance status in real-time. This visibility extends across all IT assets, whether on-premises or remote, ensuring no part of the infrastructure is left unchecked.
- Automation and Integration: By leveraging automated tools, Continuous Compliance minimizes the manual effort required to maintain compliance. These tools can automatically enforce compliance policies, detect deviations, and trigger remediation actions.
- Proactive Risk Management: Continuous Compliance frameworks are designed to not only identify compliance issues but also to predict and mitigate risks before they materialize into threats.
- Regulatory Alignment: Ensures that all compliance activities are aligned with the latest regulatory requirements, adapting to changes as they occur.
- Scalability: The approach is scalable across different sizes of organizations and can be tailored to specific industry needs, making it a versatile solution for both large enterprises and smaller entities.
Benefits of Continuous Compliance
- Reduced Risk of Non-Compliance: Continuous monitoring and automated enforcement significantly reduce the chances of compliance lapses, thereby avoiding penalties and reputational damage.
- Operational Efficiency: Automation reduces the workload on compliance and IT teams, allowing them to focus on more strategic initiatives rather than manual compliance tasks.
- Improved Security Posture: By integrating compliance with security operations, organizations can ensure that their security measures are always aligned with compliance requirements, leading to a more robust security posture.
- Cost Savings: Efficient compliance processes and reduced manual effort translate into significant cost savings over time. Automated tools also provide a better return on investment by continuously safeguarding the organization.
- Enhanced Decision Making: Real-time compliance data provides actionable insights, enabling better decision-making and more effective risk management strategies.
Implementation of Continuous Compliance
Implementing Continuous Compliance requires a structured approach involving several steps:
- Assessment and Planning: Begin with a thorough assessment of current compliance and security practices. Identify gaps and areas for improvement.
- Tool Selection and Integration: Choose the right set of automated tools that can integrate seamlessly with existing systems. Tools should support real-time monitoring, automated enforcement, and comprehensive reporting.
- Process Redesign: Redesign compliance processes to be more dynamic and integrated with daily operations. This may involve updating policies, procedures, and training programs.
- Deployment and Testing: Implement the selected tools and processes in phases. Conduct thorough testing to ensure that they function as expected and make necessary adjustments.
- Continuous Improvement: Establish a feedback loop to continuously monitor performance and make improvements. Regular audits and reviews should be conducted to ensure ongoing compliance and effectiveness.
Conclusion
Continuous Compliance represents a significant evolution in how organizations approach regulatory adherence and cyber security. By embedding compliance into the fabric of daily operations and leveraging automation, organizations can achieve a state of perpetual readiness. This not only ensures they meet regulatory requirements but also enhances their overall security posture, operational efficiency, and resilience against cyber threats.
Adopting Continuous Compliance is not just about meeting today’s standards but preparing for the future, where the pace of regulatory changes and cyber threats will only increase. As such, organizations that embrace this approach will be better positioned to navigate the complexities of the modern cyber landscape.



