Navigating the Essential 8 (E8) maturity model can be a daunting challenge, especially for complex government organizations. The ACSC’s E8 framework provides critical guidelines for improving cyber resilience, but its implementation often trips up organizations that take a linear approach—progressing from Maturity Level 1 to 2, and finally to 3. This method, while seemingly logical, can result in expensive rework as the architecture and controls deployed at lower maturity levels may not scale or align with the requirements of more advanced levels.
When it comes to program delivery, we advocate for a paradigm shift: tailor your approach to the complexity of your organization from the outset. For complex environments, this means aiming directly for Maturity Level 3 (ML3). Here’s why and how leveraging our Continuous Compliance Delivery Framework ensures success.
Why Aim for Maturity Level 3 from the Start?
- Designed for Complexity: ML3 controls are purpose-built to handle the intricacies of large and interconnected environments. Implementing ML1 or ML2 in a complex organization often leads to redundancies and inefficiencies when upgrading to ML3.
- Efficiency Through Integration: ML3 prioritizes automation, centralized management, and real-time enforcement—essential elements for modern enterprises dealing with vast amounts of endpoints and distributed systems.
- Cost and Time Savings: Iteratively scaling maturity levels wastes resources on reconfiguring architectures and processes. Starting with ML3 eliminates this duplication of effort.
Continuous Compliance: A Smarter Delivery Model
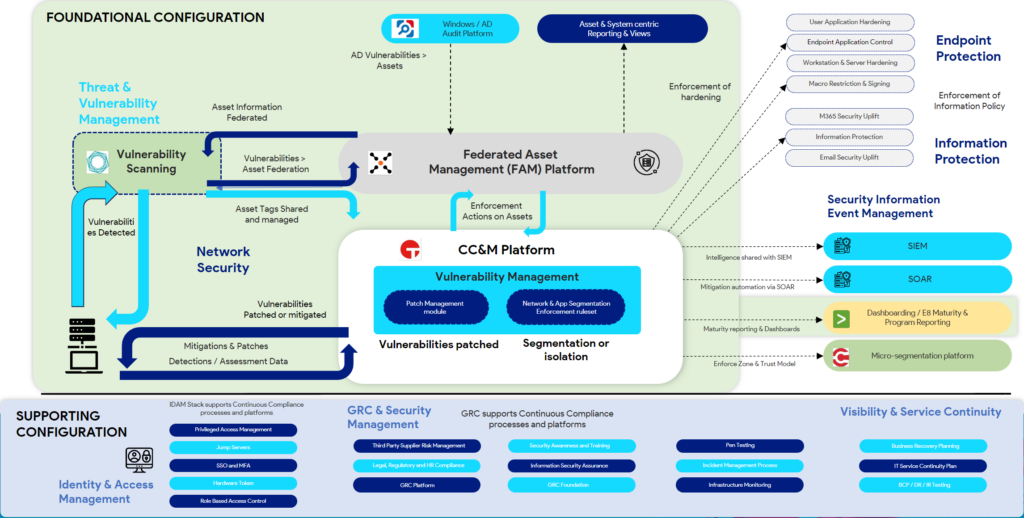
Figure 1. The approach above is one example of a typical Continuous Compliance delivery model and shows the importance of vulnerability management and Federated Asset management (FAM)
Our Continuous Compliance Delivery Framework focuses on aligning E8 controls with your organization’s unique operational environment. Here’s how our methodology ensures your journey to ML3 is streamlined:
1. End-to-End Visibility
Achieving ML3 requires comprehensive insight into your IT ecosystem. By deploying converged endpoint management solutions, such as Tanium, we help organizations gain real-time visibility of all assets—whether on-premise or remote. This visibility enables faster identification of vulnerabilities and ensures controls are enforced across the board.
2. Closed-Loop Compliance
The framework integrates monitoring, reporting, and enforcement in a continuous feedback loop. For example:
- Non-compliance is flagged in real-time via dashboards.
- Automated remediation is triggered immediately, minimizing manual intervention.
- Compliance metrics are updated dynamically to reflect the enforced changes.
3. Risk-Based Prioritization
Not all controls have equal weight in every organization. We help identify high-priority assets and vulnerabilities, ensuring resources are focused where they matter most—whether it’s patching a zero-day exploit or securing critical data repositories.
4. Customizable Reporting
Executive and operational teams have different needs. Our Splunk-integrated compliance dashboards provide tailored views of compliance status, enabling strategic decision-making and facilitating meaningful board-level discussions.
Case in Point: Driving Value with ML3
Through our approach, a government agency reduced patching timelines from months to days, streamlined vulnerability remediation processes, and achieved a 270% ROI within the first year of deployment. By skipping incremental maturity levels and focusing on ML3, the organization eliminated redundant workflows and significantly uplifted its security posture.
A Call to Action
The Essential 8 isn’t just a compliance checkbox—it’s a framework for resilience. By embracing ML3 and leveraging a continuous compliance model, organizations can safeguard critical assets efficiently and cost-effectively. At Gadget Access, we’re ready to partner with you on this journey, ensuring your cyber defenses are not just robust, but future-ready.
For more insights on how to align your organization with the Essential 8, visit the ACSC’s resource.