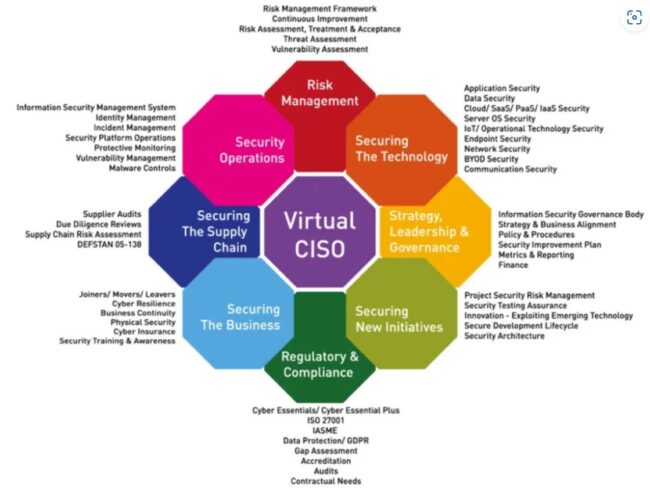
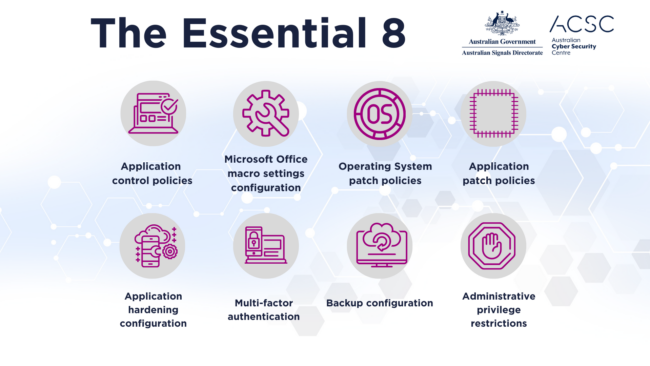
Ransomware Preparedness – Tabletop and Red Team Exercises
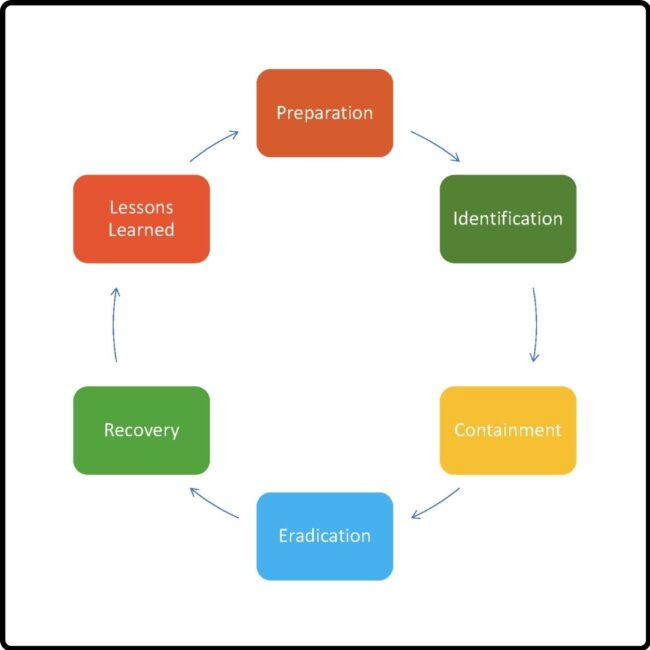
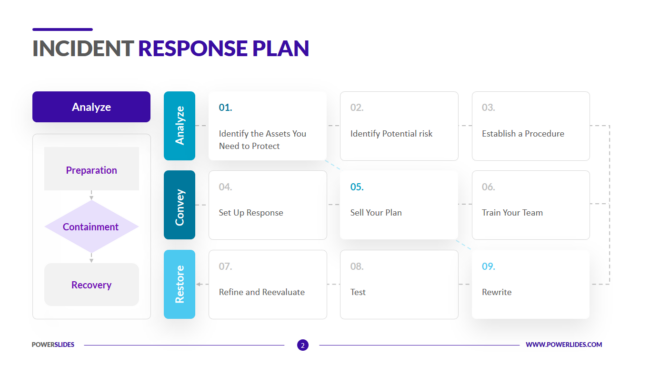
The Imperative of Ransomware Preparedness: Tabletop and Red Team Exercises Introduction Ransomware attacks are a global menace, but their impact on Australian businesses and institutions has been particularly alarming. According to the Australian Cyber Security Centre (ACSC), there was a 13% increase in ransomware attacks reported in the last financial year. With high-profile incidents like…