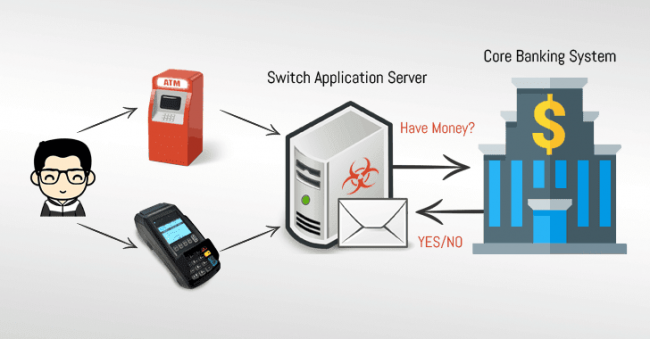
Bank Servers Hacked to Trick ATMs into Spitting Out Millions in Cash
The US-CERT has released a joint technical alert from the DHS, the FBI, and Treasury warning about a new ATM scheme being used by the prolific North Korean APT hacking group known as Hidden Cobra. Hidden Cobra, also known as Lazarus Group and Guardians of Peace, is believed to be backed by the North Korean…