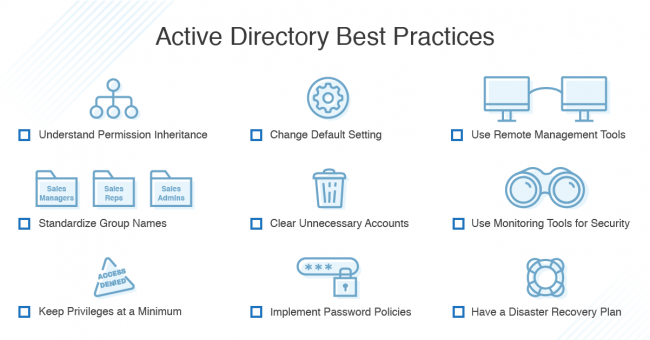
Active Directory Best Practices
Active Directory Best Practices Security Groups, User Accounts, and Other AD Basics At many enterprises and SMBs that use Windows devices, IT teams are likely to use Active Directory (AD). Essentially, Active Directory is an integral part of the operating system’s architecture, allowing IT more control over access and security. AD is a centralized, standard…