Modern Network Access – A Practical Approach to Zero Trust Network Access
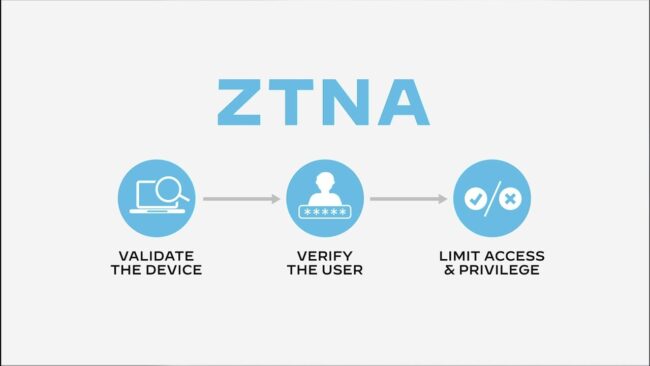
The Case for Zero Trust Network Access (ZTNA) In the evolving digital landscape, traditional network security models are increasingly inadequate. Enterprises worldwide face mounting challenges in protecting their distributed workforces and cloud-first environments from sophisticated cyber threats. For decades, network security hinged on the “castle-and-moat” or perimeter-based approach, with VPNs as a trusted mechanism…