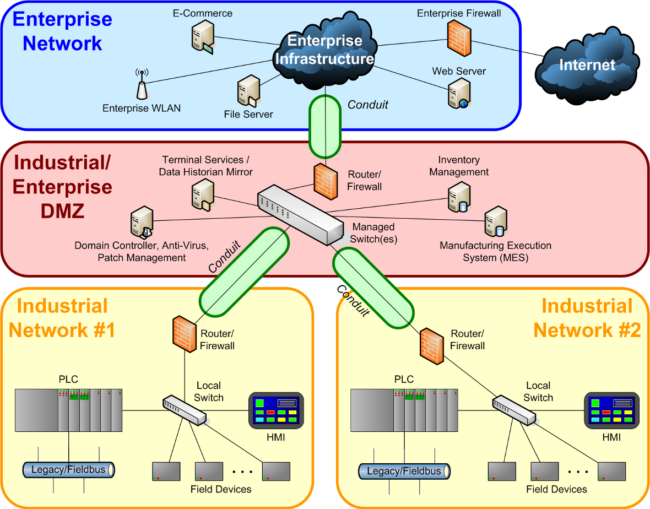
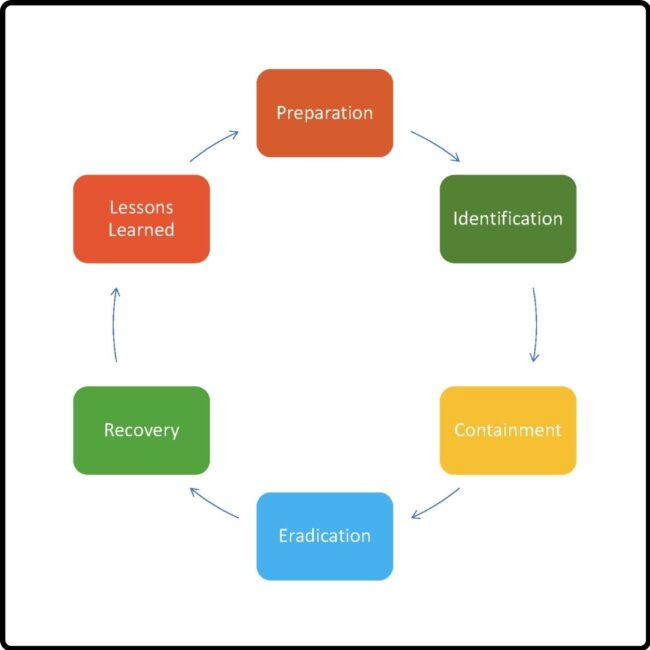
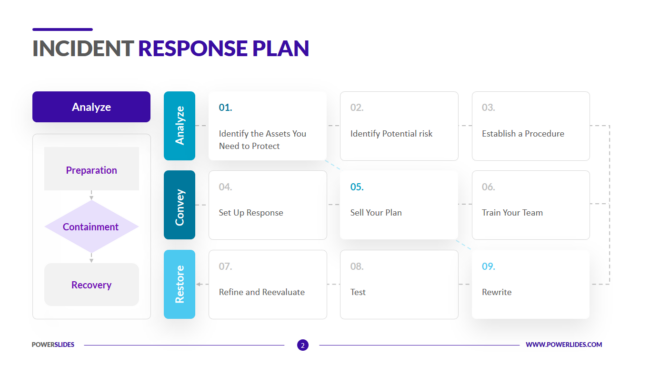
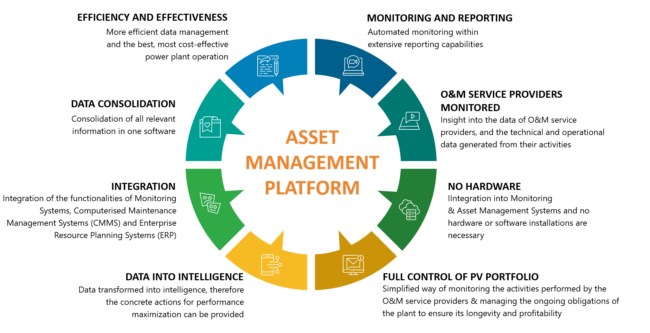
Tenable Vulnerability Management Best Practices
Introduction In the rapidly evolving landscape of cyber threats, organizations of all sizes face a relentless barrage of potential vulnerabilities. These vulnerabilities, if left unaddressed, can serve as entry points for malicious actors, leading to data breaches, financial losses, and reputational damage. As cyber threats grow in complexity, so does the need for robust vulnerability…