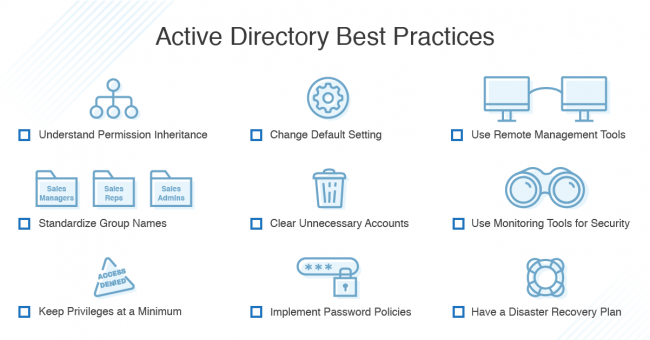
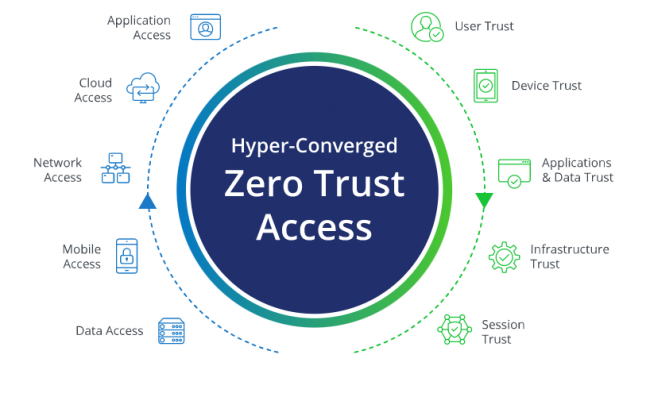
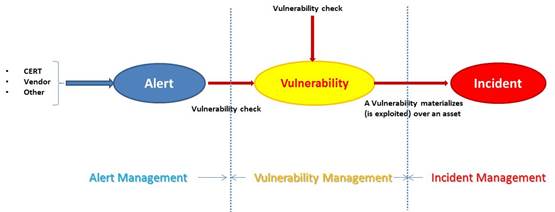
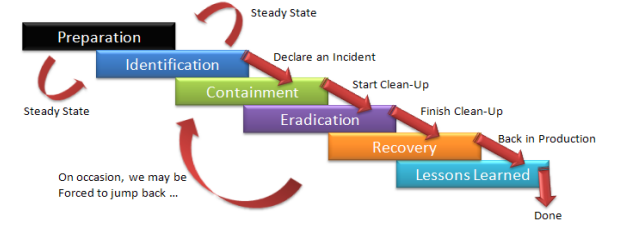
What is Zero Trust Architecture all about
Zero Trust Architecture (ZTA) is a security blueprint designed with the realities of today’s cyber threat landscape in mind. It’s based on the premise that attackers are already present, and at any point anything can be compromised – and in turn suggests organizations adhere to these key tenets of Zero Trust Architecture to maximize cyber resilience. Broadly speaking, we can classify these ZTA tenets under three security domains. Using the NIST SP 800-207 document as…